Implementing WS Security Policies for your services on webMethods Integration Server - Username and Encryption Policy
Monday, May 30, 2016SoftwareAG provides a few out of box WS-Security policies to secure the messages to protect the authenticity and integrity of the messages. You can also create your own policies as long as the security assertions used in your policy are supported by SoftwareAG Integration Server.
Before implementing the policies for your services make sure that you have completed the prerequisite steps described in the earlier post.
The Username_Encryption policy uses a username token to provide client authentication, uses symmetric binding to encrypt messages to ensure message confidentiality, and includes a timestamp token to guard against replay attacks.
Perform following steps to implement the Username_Encryption policy for your service
a. Go to the provider descriptor in the server machine. Open the policies tab and select Username and Encryption policy from the list. Click on Ok. and save the descriptor.
b. Now if you try to invoke the connector service you will get the error as 'Invalid Security', because the provider web service expects the client to pass the necessary 'WS-Security' information in the header.
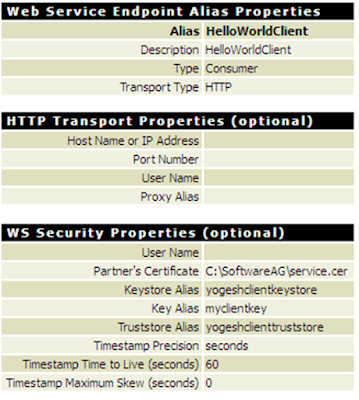
c. Attach the same policy on the consumer web service descriptor so that it will send the WS-Security information in the SOAP header while invoking the service. Make sure that you pass the 'user' and 'password' in the 'auth/message' document. This information will be used while constructing the username token.
Now when you run the service you should see a successful response.
d. Open the TCPMon screen and see the message exchange, you will notice that the timestamp has been included in the SOAP header. Also the message body itself is encrypted, so only sender and receivers are able to interpret it.
Before implementing the policies for your services make sure that you have completed the prerequisite steps described in the earlier post.
The Username_Encryption policy uses a username token to provide client authentication, uses symmetric binding to encrypt messages to ensure message confidentiality, and includes a timestamp token to guard against replay attacks.
Perform following steps to implement the Username_Encryption policy for your service
a. Go to the provider descriptor in the server machine. Open the policies tab and select Username and Encryption policy from the list. Click on Ok. and save the descriptor.
b. Now if you try to invoke the connector service you will get the error as 'Invalid Security', because the provider web service expects the client to pass the necessary 'WS-Security' information in the header.
c. Attach the same policy on the consumer web service descriptor so that it will send the WS-Security information in the SOAP header while invoking the service. Make sure that you pass the 'user' and 'password' in the 'auth/message' document. This information will be used while constructing the username token.
Now when you run the service you should see a successful response.
d. Open the TCPMon screen and see the message exchange, you will notice that the timestamp has been included in the SOAP header. Also the message body itself is encrypted, so only sender and receivers are able to interpret it.